Newitts GDPR Policy
Privacy and Personal Data Protection Policy
Contents
1. INTRODUCTION
2. PRIVACY AND PERSONAL DATA PROTECTION POLICY
2.1 THE GENERAL DATA PROTECTION REGULATION
2.2 DEFINITIONS
2.3 PRINCIPLES RELATING TO PROCESSING OF PERSONAL DATA
2.4 RIGHTS OF THE INDIVIDUAL
2.5 CONSENT
2.6 PRIVACY BY DESIGN
2.7 TRANSFER OF PERSONAL DATA
2.8 DATA PROTECTION OFFICER
2.9 BREACH NOTIFICATION
2.10 ADDRESSING COMPLIANCE TO THE GDPR
1. Introduction
In its everyday business operations Newitt & Company Ltd makes use of a variety of data about identifiable individuals, including data about:
• Current, past and prospective employees
• Customers
• Users of its websites
• Subscribers
In collecting and using this data, the organisation is subject to a variety of legislation controlling how such activities may be carried out and the safeguards that must be put in place to protect it.
The purpose of this policy is to set out the relevant legislation and to describe the steps Newitt & Company Ltd is taking to ensure that it complies with it.
This control applies to all systems, people and processes that constitute the organisation’s information systems, including board members, directors, employees, suppliers and other third parties who have access to Newitt & Company Ltd.’s systems.
The following policies and procedures are relevant to this document:
• Incident Response Policy
• Records Retention and Protection Policy
• CCTV Policy
• IT Security Policy
• Data Subject Request Procedure
2. Privacy and Personal Data Protection Policy
2.1 The General Data Protection Regulation
The General Data Protection Regulation 2016 (GDPR) is one of the most significant pieces of legislation affecting the way that Newitt & Company Ltd carries out its information processing activities. Significant fines are applicable if a breach is deemed to have occurred under the GDPR, which is designed to protect the personal data of citizens of the European Union. It is Newitt & Company Ltd.’s policy to ensure that our compliance with the GDPR and other relevant legislation is clear and demonstrable at all times.
2.2 Definitions
There are a total of 26 definitions listed within the GDPR and it is not appropriate to reproduce them all here. However, the most fundamental definitions with respect to this policy are as follows:
Personal data is defined as:
any information relating to an identified or identifiable natural person (‘data subject’); an identifiable natural person is one who can be identified, directly or indirectly, in particular by reference to an identifier such as a name, an identification number, location data, an online identifier or to one or more factors specific to the physical, physiological, genetic, mental, economic, cultural or social identity of that natural person;
‘processing’ means:
any operation or set of operations which is performed on personal data or on sets of personal data, whether or not by automated means, such as collection, recording, organisation, structuring, storage, adaptation or alteration, retrieval, consultation, use, disclosure by transmission, dissemination or otherwise making available, alignment or combination, restriction, erasure or destruction;
‘controller’ means:
the natural or legal person, public authority, agency or other body which, alone or jointly with others, determines the purposes and means of the processing of personal data; where the purposes and means of such processing are determined by Union or Member State law, the controller or the specific criteria for its nomination may be provided for by Union or Member State law;
2.3 Principles Relating to Processing of Personal Data
There are a number of fundamental principles upon which the GDPR is based.
These are as follows:
1. Personal data shall be:
(a) processed lawfully, fairly and in a transparent manner in relation to the data subject (‘lawfulness, fairness and transparency’);
(b) collected for specified, explicit and legitimate purposes and not further processed in a manner that is incompatible with those purposes; further processing for archiving purposes in the public interest, scientific or historical research purposes or statistical purposes shall, in accordance with Article 89(1), not be considered to be incompatible with the initial purposes (‘purpose limitation’);
(c) adequate, relevant and limited to what is necessary in relation to the purposes for which they are processed (‘data minimisation’);
(d) accurate and, where necessary, kept up to date; every reasonable step must be taken to ensure that personal data that are inaccurate, having regard to the purposes for which they are processed, are erased or rectified without delay (‘accuracy’);
(e) kept in a form which permits identification of data subjects for no longer than is necessary for the purposes for which the personal data are processed; personal data may be stored for longer periods insofar as the personal data will be processed solely for archiving purposes in the public interest, scientific or historical research purposes or statistical purposes in accordance with Article 89(1) subject to implementation of the appropriate technical and organisational measures required by this Regulation in order to safeguard the rights and freedoms of the data subject (‘storage limitation’);
(f) processed in a manner that ensures appropriate security of the personal data, including protection against unauthorised or unlawful processing and against accidental loss, destruction or damage, using appropriate technical or organisational measures (‘integrity and confidentiality’).
2. The controller shall be responsible for, and be able to demonstrate compliance with, paragraph 1 (‘accountability’).
Newitt & Company Ltd must ensure that it complies with all of these principles both in the processing it currently carries out and as part of the introduction of new methods of processing such as new IT systems.
2.4 Rights of the Individual
The data subject also has rights under the GDPR. These consist of:
1. The right to be informed
2. The right of access
3. The right to rectification
4. The right to erasure
5. The right to restrict processing
6. The right to data portability
7. The right to object
8. Rights in relation to automated decision making and profiling.
Each of these rights must be supported by appropriate procedures within Newitt & Company Ltd that allow the required action to be taken within the timescales stated in the GDPR.
These timescales are shown in Table 1.
| Data Subject Request |
Timescale |
| The right to be informed |
When data is collected (if supplied by data subject) or within one month (if not supplied by data subject) |
| The right of access |
One month |
| The right of rectification |
One month |
| The right of erasure |
Without undue delay |
| The right to restrict processing |
Without undue delay |
| The right to data portability |
One month |
| The right to object |
On receipt of objection |
| Rights in relation to automated decision making and profiling |
Not specified |
Table 1 - Timescales for data subject requests
2.5 Consent
Unless it is necessary for a reason allowable in the GDPR, explicit consent must be obtained from a data subject to collect and process their data. In case of children below the age of 16 parental consent must be obtained. Transparent information about our usage of their personal data must be provided to data subjects at the time that consent is obtained and their rights with regard to their data explained, such as the right to withdraw consent. This information must be provided in an accessible form, written in clear language and free of charge.
If the personal data is not obtained directly from the data subject then this information must be provided within a reasonable period after the data are obtained and definitely within one month.
2.6 Privacy by Design
Newitt & Company Ltd has adopted the principle of privacy by design and will ensure that the definition and planning of all new or significantly changed systems that collect or process personal data will be subject to due consideration of privacy issues, including the completion of one or more data protection impact assessments.
The data protection impact assessment will include:
• Consideration of how personal data will be processed and for what purposes
• Assessment of whether the proposed processing of personal data is both necessary and proportionate to the purpose(s)
• Assessment of the risks to individuals in processing the personal data
• What controls are necessary to address the identified risks and demonstrate compliance with legislation
Use of techniques such as data minimization and pseudonymisation should be considered where applicable and appropriate.
2.7 Transfer of Personal Data
Transfers of personal data outside the European Union must be carefully reviewed prior to the transfer taking place to ensure that they fall within the limits imposed by the GDPR. This depends partly on the European Commission’s judgement as to the adequacy of the safeguards for personal data applicable in the receiving country and this may change over time.
Intra-group international data transfers must be subject to legally binding agreements referred to as Binding Corporate Rules (BCR) which provide enforceable rights for data subjects.
2.8 Data Protection Officer
A defined role of Data Protection Officer (DPO) is required under the GDPR if an organisation is a public authority, if it performs large scale monitoring or if it processes particularly sensitive types of data on a large scale. The DPO is required to have an appropriate level of knowledge and can either be an in-house resource or outsourced to an appropriate service provider.
Based on these criteria, Newitt & Company Ltd does not require a Data Protection Officer to be appointed.
2.9 Breach Notification
It is Newitt & Company Ltd.’s policy to be fair and proportionate when considering the actions to be taken to inform affected parties regarding breaches of personal data. In line with the GDPR, where a breach is known to have occurred which is likely to result in a risk to the rights and freedoms of individuals, the relevant Data Protection Authority (DPA) will be informed within 72 hours. This will be managed in accordance with our Information Security Incident Response Procedure which sets out the overall process of handling information security incidents.
Under the GDPR the relevant DPA has the authority to impose a range of fines of up to four percent of annual worldwide turnover or twenty million Euros, whichever is the higher, for infringements of the regulations.
2.10 Addressing Compliance to the GDPR
The following actions are undertaken to ensure that Newitt & Co.Ltd complies at all times with the accountability principle of the GDPR:
• The legal basis for processing personal data is clear and unambiguous
• All staff involved in handling personal data understand their responsibilities for following good data protection practice
• Training in data protection has been provided to all staff
• Rules regarding consent are followed
• Routes are available to data subjects wishing to exercise their rights regarding personal data and such enquiries are handled effectively
• Regular reviews of procedures involving personal data are carried out
• Privacy by design is adopted for all new or changed systems and processes
• The following documentation of processing activities is recorded:
o Organisation name and relevant details
o Purposes of the personal data processing
o Categories of individuals and personal data processed
o Categories of personal data recipients
o Agreements and mechanisms for transfers of personal data to non-EU countries including details of controls in place
o Personal data retention schedules
o Relevant technical and organisational controls in place
These actions will be reviewed on a regular basis as part of the management review process of the information security management system.
Records Retention and Protection Policy
Contents
1. INTRODUCTION
2. RECORDS RETENTION AND PROTECTION POLICY
2.1 GENERAL PRINCIPLES
2.2 RECORD TYPES AND GUIDELINES
2.3 USE OF CRYPTOGRAPHY
2.4 MEDIA SELECTION
2.5 RECORD RETRIEVAL
2.6 RECORD DESTRUCTION
2.7 RECORD REVIEW
1. Introduction
In its everyday business operations Newitt & Co. Ltd collects and stores records of many types and in a variety of different formats. The relative importance and sensitivity of these records also varies and is subject to the organisation’s security classification scheme.
It is important that these records are protected from loss, destruction, falsification, unauthorised access and unauthorised release and range of controls are used to ensure this, including backups, access control and encryption.
Newitt & Co. Ltd also has a responsibility to ensure that it complies with all relevant legal, regulatory and contractual requirements in the collection, storage, retrieval and destruction of records. Of particular relevance is the European Union General Data Protection Regulation (GDPR) and its requirements concerning the storage and processing of personal data.
This control applies to all systems, people and processes that constitute the organisation’s information systems, including board members, directors, employees, suppliers and other third parties who have access to Newitt & Co. Ltd systems.
The following policies and procedures are relevant to this document:
• Privacy and Personal Data Protection Policy
• Information Asset Register
• IT Security Policy
• Data Subject Request Procedure
• Incident Response Policy
2. Records Retention and Protection Policy
This policy begins by establishing the main principles that must be adopted when considering record retention and protection. It then sets out the types of records held by Newitt & Co Ltd and their general requirements before discussing record protection, destruction and management.
2.1 General Principles
There are a number of key general principles that should be adopted when considering record retention and protection policy. These are:
• Records should be held in compliance with all applicable legal, regulatory and contractual requirements
• Records should not be held for any longer than required
• The protection of records in terms of their confidentiality, integrity and availability should be in accordance with their security classification
• Records should remain retrievable in line with business requirements at all times
• Where appropriate, records containing personal data should be subject as soon as possible to techniques that prevent the identification of a living individual
2.2 Record Types and Guidelines
In order to assist with the definition of guidelines for record retention and protection, records held by Newitt & Co Ltd are grouped into the categories listed in Information Asset Register, a copy of which is at Schedule 1. For each of these categories, the required or recommended retention period and allowable storage media are also given, together with a reason for the recommendation or requirement.
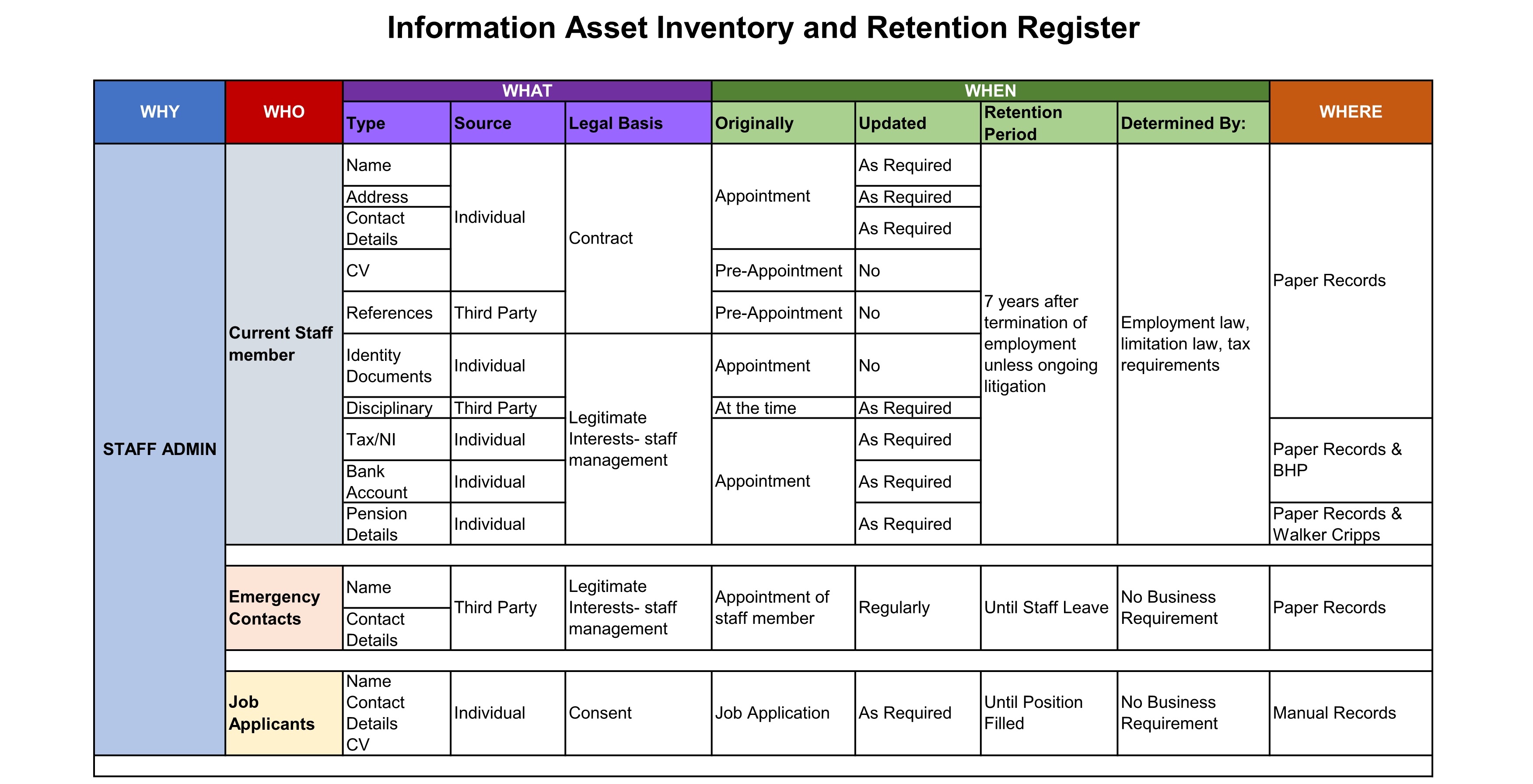
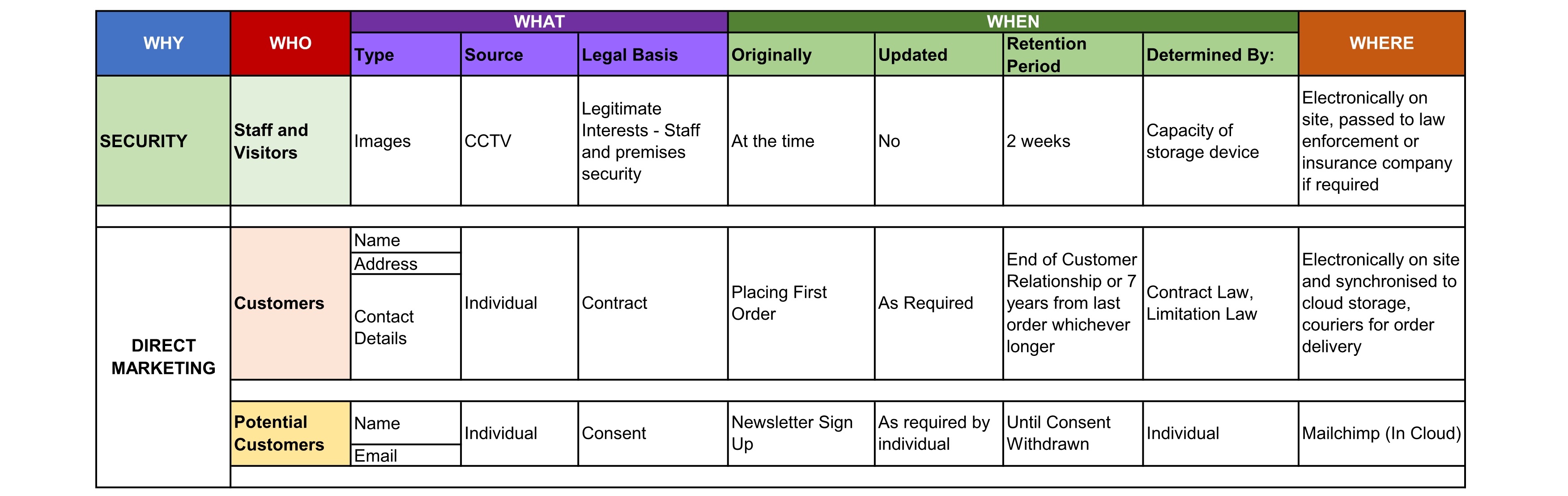 Table 2 - Record types and retention periods
Table 2 - Record types and retention periods
Where appropriate to the classification of information and the storage medium, cryptographic techniques should be used to ensure the confidentiality and integrity of records.
Care should be taken to ensure that encryption keys used to encrypt records are securely stored for the life of the relevant records and comply with the organization’s policy on cryptography.
2.3 Media Selection
The choice of long term storage media should take into account the physical characteristics of the medium and the length of time it will be in use.
Where records are legally (or practically) required to be stored on paper, adequate precautions must be taken to ensure that environmental conditions remain suitable for the type of paper used. Where possible, backup copies of such records should be taken by methods such as scanning. Regular checks should be made to assess the rate of deterioration of the paper and action taken to preserve the records if required.
For records stored on electronic media, similar precautions must be taken to ensure the longevity of the materials, including correct storage and copying onto more robust media if necessary. The ability to read the contents of the particular media format should be maintained by the keeping of a device capable of processing it. If this is impractical an external third party may be employed to convert the media onto an alternative format.
2.4 Record Retrieval
There is little point in retaining records if they are not able to be accessed in line with business or legal requirements. The choice and maintenance of record storage facilities should ensure that records can be retrieved in a usable format within an acceptable period of time. An appropriate balance should be struck between the cost of storage and the speed of retrieval so that the most likely circumstances are adequately catered for.
2.5 Record Destruction
Once records have reached the end of their life according to the defined policy, they should be securely destroyed in a manner that ensures that they can no longer be used. The destruction procedure should allow for the correct recording of the details of disposal which should be retained as evidence.
2.6 Record Review
The retention and storage of records should be subject to a regular review process carried out under the guidance of management to ensure that:
• The policy on records retention and protection remains valid
• Records are being retained according to the policy
• Records are being securely disposed of when no longer required
• Legal, regulatory and contractual requirements are being fulfilled
• Processes for record retrieval are meeting business requirements
The results of these reviews should be recorded.
Newitt & Company Limited Information Security Policy
The Directors and management of Newitt & Company Limited are committed to preserving the confidentiality, integrity and availability of all the electronic information assets throughout the organisation in order to ensure its legal, regulatory and contractual compliance. Information and information security requirements will be reviewed regularly to ensure they are aligned with Newitt & Company Limited’s commercial requirements to maintain IT security-related risks at acceptable levels.
Business continuity and contingency plans, data backup procedures, avoidance of viruses and hackers, access control to systems and information security incident reporting are fundamental to this policy.
All Newitt & Company Limited employees and certain external parties identified in the information security policy are expected to comply with this policy.
This policy will be reviewed to respond to any changes in the risk assessment and at least annually.
The sections of this document can be copied into information requests, wherever necessary. However if details of Newitt & Company Limited security measures detailed within the policy are required a Non Disclosure Agreement must first be entered into.
Scope of the Information Security Policy
This policy covers all aspects of Information Systems security required to ensure the protection and integrity of Newitt & Company Limited IT information assets. Specifically:
Maintaining Information Security
All full time or part time employees, sub-contractors, project consultants and external parties have, and will be made aware of, their responsibilities to preserve information security, to report security breaches and to act in accordance with the requirements of this Information Security Policy.
All employees will receive information security awareness training.
Accessibility of Information
Information must be organised to be accessible to authorised users when required but secure from unauthorised access.
The computer networks must be resilient and Newitt & Company Limited must be able to detect and respond rapidly to incidents (such as viruses and other malware) that threaten the continued availability and the security of IT assets, systems and information.
There must be appropriate backup recovery; disaster recovery and business continuity plans.
Confidentiality
This involves ensuring that information is only accessible to those authorised to access it and preventing both deliberate and accidental unauthorised access to Newitt & Company Limited information, proprietary knowledge and systems including networks, e-commerce systems and websites.
Data integrity
Safeguarding the accuracy and completeness of information and processing methods, requires preventing deliberate or accidental, partial or complete, destruction or unauthorised modification, of electronic data. There must be appropriate contingency covering all systems including networks, e-commerce systems, websites, data backup plans and security incident reporting.
Newitt & Company Limited must comply with all relevant UK data-related legislation.
Security of physical computing assets
Newitt & Company Limited physical assets including computer hardware, data cabling, telephone systems, filing systems and physical data files must all be secure.
Security of information assets
The information assets stored electronically on servers, websites, intranets, PCs, laptops, mobile phones and PDAs, CD ROMs, USB sticks, backup tapes and any other digital or magnetic media, and information transmitted electronically by any means are all subject to this policy.
All staff who are part of our IT service delivery framework are required to accept and sign up to our IT Security Policy.
Business Continuity and Disaster Recovery
Newitt & Company Limited has a comprehensive Business Continuity Plan that sets out the steps Newitt & Company Limited will take to survive a disaster, whether minor, moderate or major, i.e. the loss of a significant part of the business operation for more than a few hours.
Security Breach
A security breach is any incident or activity that causes, or may cause, a break down in the availability, confidentiality or integrity of Newitt & Company Limited’s electronic information assets. Newitt & Company Limited’s response to a security breach forms part of this IT Security policy.
Security Measures
This section describes the technical and procedural security measures implemented by Newitt & Company Limited for secure information access and storage.
Newitt & Company Limited Site Security
All access to Newitt & Company Limited’s site is controlled.
Access to the Newitt & Company Limited Enterprise IT infrastructure
Access to Newitt & Company Limited’s enterprise systems from within the Newitt & Company Limited office network is controlled through a centralised Microsoft Active Directory service providing full authentication, authorisation and audit trail.
Newitt & Company Limited Personnel Procedures
All user authentication to IT resources via network access and systems access is integrated and centralised to the Newitt & Company Limited Active Directory environment, configured for accounting of user activity and authorisation restriction, where required.
This implementation allows for central control over access to Newitt & Company Limited information for joiners and leavers, enabling Human Resources to effectively integrate IT Systems access to existing HR policy.
Email Security
The Newitt & Company Limited email solution has the following services for email information and security:
- All Domains related to Newitt & Company Limited are centrally managed and controlled.
- Email security, including antivirus and spam protection is provided by GFI.
- Email access is authenticated and accounted for with Microsoft Active Directory.
- All email access from public networks is SSL encrypted.
- Email can only be stored on the Newitt & Company Limited Office 365 accounts.
Access to Authenticated Data
Granular control of file and system access is defined by the permissions structure within the Newitt & Company Limited Microsoft Active Directory solution.
User access activity is fully accounted and audited.
Administrative access activity is strictly controlled, regularly audited and accounted.
Local Data Storage and Backup
All Newitt & Company Limited data is stored on secured storage systems.
All server locations have maintained uninterruptable power supply units.
Storage system access is strictly controlled with active directory permission levels.
Decommissioning of server or storage data and systems is controlled to ensure complete data destruction.
Document Owner and Approval
The Managing Director is the owner of this document and is responsible for ensuring that this policy document is reviewed in line with the requirements of Newitt & Company Limited Directors and management.
A current version of this document is available to all members of staff. It does not contain confidential information and can be released to relevant external parties.
CCTV Policy
Introduction
Newitt & Company Limited (“the Company”) uses closed circuit television (CCTV) images to provide a safe and secure environment for employees and for visitors to the Company’s business premises, such as clients, customers, contractors and suppliers, and to protect the Company’s property.
This policy sets out the use and management of the CCTV equipment and images in compliance with relevant legislation and the CCTV Code of Practice.
The Company’s CCTV facility records images only. There is no audio recording i.e. conversations are not recorded on CCTV.
Purposes of CCTV
The purposes of the Company installing and using CCTV systems include:
• To assist in the prevention or detection of crime or equivalent malpractice.
• To assist in the identification and prosecution of offenders.
• To monitor the security of the Company’s business premises.
• To ensure that health and safety rules and Company procedures are being complied with.
• To assist with the identification of unauthorised actions or unsafe working practices that might result in disciplinary proceedings being instituted against employees and to assist in providing relevant evidence.
• To promote productivity and efficiency.
Location of cameras
Cameras are located at strategic points throughout the Company’s business premises, principally at the entrance and exit points. The Company has positioned the cameras so that they only cover communal or public areas on the Company’s business premises and they have been sited so that they provide clear images. No camera focuses or will focus, on toilets, shower facilities, changing rooms, staff kitchen areas, staff break rooms or private offices.
All cameras are also clearly visible.
Appropriate signs are prominently displayed so that employees, clients, customers and other visitors are aware they are entering an area covered by CCTV.
Recording and retention of images
Images produced by the CCTV equipment are intended to be as clear as possible so that they are effective for the purposes set out above. Maintenance checks of the equipment are undertaken on a regular basis to ensure it is working properly and that the media is producing high-quality images.
Images may be recorded either in constant real-time (24 hours a day throughout the year) or only at certain times, as the needs of the business dictate.
As the recording system records digital images, any CCTV images that are held on the hard drive of a PC or server are deleted and overwritten on a recycling basis and, in any event, are not held for more than one month. Once a hard drive has reached the end of its use, it will be erased prior to disposal.
Images that are stored on, or transferred on to, removable media such as CDs are erased or destroyed once the purpose of the recording is no longer relevant. In normal circumstances, this will be a period of one month. However, where a law enforcement agency is investigating a crime, images may need to be retained for a longer period.
Access to and disclosure of images
Access to, and disclosure of, images recorded on CCTV is restricted. This ensures that the rights of individuals are retained. Images can only be disclosed in accordance with the purposes for which they were originally collected.
The images that are filmed are recorded centrally and held in a secure location. Access to recorded images is restricted to the operators of the CCTV system and to those line managers who are authorised to view them in accordance with the purposes of the system. Viewing of recorded images will take place in a restricted area to which other employees will not have access when viewing is occurring. If media on which images are recorded is removed for viewing purposes, this will be documented.
Disclosure of images to other third parties will only be made in accordance with the purposes for which the system is used and will be limited to:
• The police and other law enforcement agencies, where the images recorded could assist in the prevention or detection of a crime or the identification and prosecution of an offender or the identification of a victim or witness.
• Prosecution agencies, such as the Crown Prosecution Service.
• Relevant legal representatives.
• Line managers involved with Company disciplinary and performance management processes.
• Individuals whose images have been recorded and retained (unless disclosure would prejudice the prevention or detection of crime or the apprehension or prosecution of offenders).
The Managing Director of the Company (or another senior director acting in their absence) is the only person who is permitted to authorise disclosure of images to external third parties such as law enforcement agencies.
All requests for disclosure and access to images will be documented, including the date of the disclosure, to whom the images have been provided and the reasons why they are required. If disclosure is denied, the reason will be recorded.
Individuals’ access rights
Individuals have the right on request to receive a copy of the personal data that the Company holds about them, including CCTV images if they are recognisable from the image.
If you wish to access any CCTV images relating to you, you must make a written request to the Company’s Managing Director. Your request must include the date and approximate time when the images were recorded and the location of the particular CCTV camera so that the images can be easily located and your identity can be established as the person in the images. The Company will respond promptly and in any case within one month of receiving the request.
The Company will always check the identity of the employee making the request before processing it.
The Managing Director will first determine whether disclosure of your images will reveal third-party information as you have no right to access CCTV images relating to other people. In this case, the images of third parties may need to be obscured if it would otherwise involve an unfair intrusion into their privacy.
If the Company is unable to comply with your request because access could prejudice the prevention or detection of crime or the apprehension or prosecution of offenders, you will be advised accordingly.
Covert recording
The Company will only undertake covert recording with the written authorisation of the Managing Director (or another senior director acting in their absence) where there is good cause to suspect that criminal activity or equivalent malpractice is taking, or is about to take, place and informing the individuals concerned that the recording is taking place would seriously prejudice its prevention or detection.
Covert monitoring may include both video and audio recording.
Covert monitoring will only take place for a limited and reasonable amount of time consistent with the objective of assisting in the prevention and detection of particular suspected criminal activity or equivalent malpractice. Once the specific investigation has been completed, covert monitoring will cease.
Information obtained through covert monitoring will only be used for the prevention or detection of criminal activity or equivalent malpractice. All other information collected in the course of covert monitoring will be deleted or destroyed unless it reveals information which the Company cannot reasonably be expected to ignore.
Staff training
The Company will ensure that all employees handling CCTV images or recordings are trained in the operation and administration of the CCTV system and on the impact of relevant legislation with regard to that system.
Implementation
The Company’s Managing Director is responsible for the implementation of and compliance with this policy and the operation of the CCTV system and they will conduct a regular review of the Company’s use of CCTV. Any complaints or enquiries about the operation of the Company’s CCTV system should be addressed to them.
Incident Response Policy
Newitt & Company Limited (“the Company”) is hereinafter referred to as "the company."
1.0 Overview
A security incident can come in many forms: a malicious attacker gaining access to the network, a virus or other malware infecting computers, or even a stolen laptop containing confidential data. A well-thought-out Incident Response Policy is critical to successful recovery from an incident. This policy covers all incidents that may affect the security and integrity of the company's information assets, and outlines steps to take in the event of such an incident.
2.0 Purpose
This policy is intended to ensure that the company is prepared if a security incident were to occur. It details exactly what must occur if an incident is suspected, covering both electronic and physical security incidents. Note that this policy is not intended to provide a substitute for legal advice, and approaches the topic from a security practices perspective.
3.0 Scope
The scope of this policy covers all information assets owned or provided by the company, whether they reside on the corporate network or elsewhere.
4.0 Policy
4.1 Types of Incidents
A security incident, as it relates to the company's information assets, can take one of two forms. For the purposes of this policy a security incident is defined as one of the following:
• Electronic: This type of incident can range from an attacker or user accessing the network for unauthorized/malicious purposes, to a virus outbreak, to a suspected Trojan or malware infection.
• Physical: A physical IT security incident involves the loss or theft of a laptop, mobile device, PDA/Smartphone, portable storage device, or other digital apparatus that may contain company information.
4.2 Preparation
Work done prior to a security incident is arguably more important than work done after an incident is discovered. The most important preparation work, obviously, is maintaining good security controls that will prevent or limit damage in the event of an incident. This includes technical tools such as firewalls, intrusion detection systems, authentication, and encryption; and non-technical tools such as good physical security for laptops and mobile devices.
Additionally, prior to an incident, the company must ensure that the following is clear to IT personnel:
• What actions to take when an incident is suspected.
• Who is responsible for responding to an incident.
The company should review any industry or governmental regulations that dictate how it must respond to a security incident (specifically, loss of personal data), and ensure that its incident response plans adhere to these regulations.
4.3 Confidentiality
All information related to an electronic or physical security incident must be treated as confidential information until the incident is fully contained. This will serve both to protect employees' reputations (if an incident is due to an error, negligence, or carelessness), and to control the release of information to the media and/or customers.
4.4 Electronic Incidents
When an electronic incident is suspected, the company's goal is to recover as quickly as possible, limit the damage done, and secure the network. The following steps should be taken in order:
1. Remove the compromised device from the network by unplugging or disabling network connection. Do not power down the machine.
2. Disable the compromised account(s) as appropriate.
3. Report the incident to the IT Manager.
4. Backup all data and logs on the machine, or copy/image the machine to another system.
5. Determine exactly what happened and the scope of the incident. Was it an accident? An attack? A Virus? Was confidential data involved? Was it limited to only the system in question or was it more widespread?
6. Notify company management/executives as appropriate.
7. Contact an IT Security consultant as needed.
8. Determine how the attacker gained access and disable this access.
9. Rebuild the system, including a complete operating system reinstall.
10. Restore any needed data from the last known good backup and put the system back online.
11. Take actions, as possible, to ensure that the vulnerability (or similar vulnerabilities) will not reappear.
12. Reflect on the incident. What can be learned? How did the Incident Response team perform? Was the policy adequate? What could be done differently?
13. Consider a vulnerability assessment as a way to spot any other vulnerabilities before they can be exploited.
4.5 Physical Incidents
Physical security incidents are challenging, since often the only actions that can be taken to mitigate the incident must be done in advance. This makes preparation critical. One of the best ways to prepare is to mandate the use of strong encryption to secure data on mobile devices. Applicable polices, such as those covering encryption and confidential data, should be reviewed.
Physical security incidents are most likely the result of a random theft of inadvertent loss by a user, but they must be treated as if they were targeted at the company.
The company must assume that such a loss will occur at some point, and periodically survey a random sampling of laptops and mobile devices to determine the risk if one were to be lost or stolen.
4.5.1 Response
Establish the severity of the incident by determining the data stored on the missing device. This can often be done by referring to a recent backup of the device. Two important questions must be answered:
1. Was confidential data involved?
a. If not, refer to "Loss Contained" below.
b. If confidential data was involved, refer to "Data Loss Suspected" below.
2. Was strong encryption used?
a. If strong encryption was used, refer to "Loss Contained" below.
b. If not, refer to "Data Loss Suspected" below.
4.5.2 Loss Contained
First, change any usernames, passwords, account information, WEP/WPA keys, passphrases, etc., that were stored on the system. Notify the IT Manager. Replace the lost hardware and restore data from the last backup. Notify the applicable authorities if a theft has occurred.
4.5.3 Data Loss Suspected
First, notify the executive team, legal advisers, and/or public relations so that each team can evaluate and prepare a response in their area.
Change any usernames, passwords, account information, WEP/WPA keys, passphrases, etc., that were stored on the system. Replace the lost hardware and restore data from the last backup. Notify the applicable authorities as needed if a theft has occurred and follow disclosure guidelines specified in the notification section.
Review procedures to ensure that risk of future incidents is reduced by implementing stronger physical security controls.
4.6 Notification
If an electronic or physical security incident is suspected to have resulted in the loss of third-party/customer data, notification of the public or affected entities should occur. First this must be discussed with executive team and legal counsel to determine an appropriate course of action. If notification is deemed an appropriate, it should occur in an organized and consistent manner. If required, notification must be made within 72 hours.
4.7 Managing Risk
Managing risk of a security incident or data loss is the primary reason to create and maintain a comprehensive security policy. Risks can come in many forms: electronic risks like data corruption, computer viruses, hackers, or malicious users; or physical risks such as loss/theft of a device, hardware failure, fire, or a natural disaster. Protecting critical data and systems from these risks is of paramount importance to the company.
4.8 Applicability of Other Policies
This document is part of the company's cohesive set of security policies. Other policies may apply to the topics covered in this document and as such the applicable policies should be reviewed as needed.
5.0 Enforcement
This policy will be enforced by the IT Manager and/or Executive Team. Violations may result in disciplinary action, which may include suspension, restriction of access, or more severe penalties up to and including termination of employment. Where illegal activities or theft of company property (physical or intellectual) are suspected, the company may report such activities to the applicable authorities.
6.0 Definitions
- Encryption - The process of encoding data with an algorithm so that it is unintelligible without the key. Used to protect data during transmission or while stored.
- Malware - Short for "malicious software." A software application designed with malicious intent. Viruses and Trojans are common examples of malware.
- Mobile Device - A portable device that can be used for certain applications and data storage. Examples are PDAs or Smartphones.
- PDA - Stands for Personal Digital Assistant. A portable device that stores and organizes personal information, such as contact information, calendar, and notes.
- Smartphone - A mobile telephone that offers additional applications, such as PDA functions and email.
- Trojan - Also called a "Trojan Horse." An application that is disguised as something innocuous or legitimate, but harbours a malicious payload. Trojans can be used to covertly and remotely gain access to a computer, log keystrokes, or perform other malicious or destructive acts.
- Virus - Also called a "Computer Virus." A replicating application that attaches itself to other data, infecting files similar to how a virus infects cells. Viruses can be spread through email or via network-connected computers and file systems.
- WEP - Stands for Wired Equivalency Privacy. A security protocol for wireless networks that encrypts communications between the computer and the wireless access point. WEP can be cryptographically broken with relative ease.
- WPA - Stands for WiFi Protected Access. A security protocol for wireless networks that encrypts communications between the computer and the wireless access point. Newer and considered more secure than WEP.
Privacy and Cookie Policy for Website
Newitt & Co Ltd - Privacy Policy
Who we are
In this privacy policy references to “we”, “us” and “our” are to Newitt & Co Ltd. References to “our Website” or “the Website” are to www.newitts.com.
What information we collect and how
The information we collect via the Website may include:
• Any personal details you knowingly provide us with through forms and our email, such as name, address, telephone number etc.
• In order to effectively process credit or debit card transactions it may be necessary for the bank or card processing agency to verify your personal details for authorisation outside the European Economic Area (EEA). Such information will not be transferred out of the EEA for any other purpose.
• Your preferences and use of email updates, recorded by emails we send you (if you select to receive email updates on products and offers).
• Your IP Address, this is a string of numbers unique to your computer that is recorded by our web server when you request any page or component on the Website. This information is used to monitor your usage of the Website.
• Data recorded by the Website which allows us to recognise you and your preferred settings, this saves you from re-entering information on return visits to the site. Such data is recorded locally on your computer through the use of cookies. Most browsers can be programmed to reject, or warn you before downloading cookies, information regarding this may be found in your browsers ‘help’ facility.
What we do with your information
Any personal information we collect from this website will be used in accordance with the Data Protection Act 1998/General Data Protection Regulations and other applicable laws. The details we collect will be used:
• identify you and manage any accounts you hold with us;
• process your order;
• conduct research, statistical analysis and behavioural analysis;
• carry out customer profiling and analyse your purchasing preferences;
• if you agree, let you know about other products or services that may be of interest to you—see 'Marketing’ section below;
• detect and prevent fraud;
• customise our website and its content to your particular preferences;
• notify you of any changes to our website or to our services that may affect you; and
• improve our services.
Marketing
We would like to send you information by post, email, telephone, text message (SMS) or automated call about products and services, competitions and special offers which may be of interest to you.
We will only ask whether you would like us to send you marketing messages when you tick the relevant boxes when you complete an order or sign up to our newsletter.
If you have consented to such receive marketing from us, you can opt out at any time. See 'What rights do you have?’ below for further information.
Monitoring and recording communications
We may monitor and record communications with you (such as telephone conversations and emails) for the purpose of quality assurance, training, fraud prevention and compliance.
Keeping your data secure
We will use technical and organisational measures to safeguard your personal data, for example:
• access to your account is controlled by a password and user name that are unique to you;
• we store your personal data on secure servers; and
• payment details are encrypted using SSL technology (typically you will see a lock icon or green address bar (or both) in your browser when we use this technology).
While we will use all reasonable efforts to safeguard your personal data, you acknowledge that the use of the internet is not entirely secure and for this reason we cannot guarantee the security or integrity of any personal data that are transferred from you or to you via the internet. If you have any particular concerns about your information, please contact us (see ‘How can you contact us?’ below).
What can I do to keep my information safe?
If you want detailed information from Get Safe Online on how to protect your information and your computers and devices against fraud, identity theft, viruses and many other online problems, please visit www.getsafeonline.org. Get Safe Online is supported by HM Government and leading businesses.
What rights do you have?
Right to request a copy of your information
You can request a copy of your information which we hold (this is known as a subject access request). If you would like a copy of some or it, please:
• email, call or write to us (see ‘How can you contact us?’ below)
• let us have proof of your identity and address (a copy of your driving licence or passport and a recent utility or credit card bill), and
• let us know the information you want a copy of, including any account or reference numbers, if you have them
Right to correct any mistakes in your information
You can require us to correct any mistakes in your information which we hold free of charge. If you would like to do this, please:
• email, call or write to us (see ‘How can you contact us?’ below)
• let us have enough information to identify you (eg account number, user name, registration details), and
• let us know the information that is incorrect and what it should be replaced with
Right to ask us to stop contacting you with direct marketing
You can ask us to stop contacting you for direct marketing purposes. If you would like to do this, please:
• email, call or write to us (see ‘How can you contact us?’ below). You can also click on the ‘unsubscribe’ button at the bottom of the email newsletter
• let us have proof of your identity and address (a copy of your driving licence or passport and a recent utility or credit card bill), and
• let us know what method of contact you are not happy with if you are unhappy with certain ways of contacting you only (for example, you may be happy for us to contact you by email but not by telephone)
How to contact us
Please contact if you have any questions about this privacy policy or the information we hold about you.
If you wish to contact us, please send an email to [email protected] or write to us at:
Newitt & Co Ltd
Claxton Hall
Flaxton
York
North Yorkshire
YO60 7RE
United Kingdom
or call us on 01904 468551
Changes to the privacy policy
We may change this privacy policy from time to time. You should check this policy occasionally to ensure you are aware of the most recent version that will apply each time you access this website.
Data Breach Report Form
If you know or suspect a data security breach has occurred, please:
-
Download a copy of our Data Breach Report Form? Please Click Here
-
Complete the form and
- email or deliver it to Nicholas Newitt ensuring you mark your email or the form as urgent.
You can view our privacy policy HERE -
You can view our full Cookie policy HERE -
